Your Security operation center architecture design images are ready in this website. Security operation center architecture design are a topic that is being searched for and liked by netizens today. You can Download the Security operation center architecture design files here. Get all royalty-free vectors.
If you’re looking for security operation center architecture design images information related to the security operation center architecture design keyword, you have come to the right site. Our website always provides you with suggestions for viewing the highest quality video and image content, please kindly surf and locate more enlightening video articles and images that match your interests.
Security Operation Center Architecture Design. This position fulfils the most critical role of primarily deploying the customized big data open source SOC technologies along with traditional commercial products at times in the right location and configuration to identify the. As a Security Architect he built and released an auto-mitigation framework that has been used to automatically fight attacks in large organizations. Download your free copy of the 10 Essential Capabilities of a Modern SOC. Examining the key design elements in a successful SOC implementation.

Security operations center best practices include preemptively addressing weak points to neutralize potential attacks before they occur minimizing the number of incidents requiring an active response. Defines design thumb rules and parameters for SOC Design. This chapter from Security Operations Center. Penetration testing will simulate cyberattacks to determine potential entry methods and other vulnerabilities. Remediation Recovery and Assessment Audit. Download your free copy of the 10 Essential Capabilities of a Modern SOC.
Security Operations Center SOC.
Cybersecurity Operations Center CSOC Computer Emergency Response Team CERT In order for an organization to be considered a SOC it must. Ad Help analysts navigate high-value activities and high fidelity threats. At checkout use discount code PBTY25 for 25 off these and other Elsevier titles. Security operations center staff consists primarily of security analysts who work together to detect analyze respond to report. Ad Help analysts navigate high-value activities and high fidelity threats. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security.
 Source: pinterest.com
Source: pinterest.com
Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Over the past decade information technology has. Download your free copy of the 10 Essential Capabilities of a Modern SOC. These include Event Classification. Ray Bernard PSP CHS-III.
 Source: exabeam.com
Source: exabeam.com
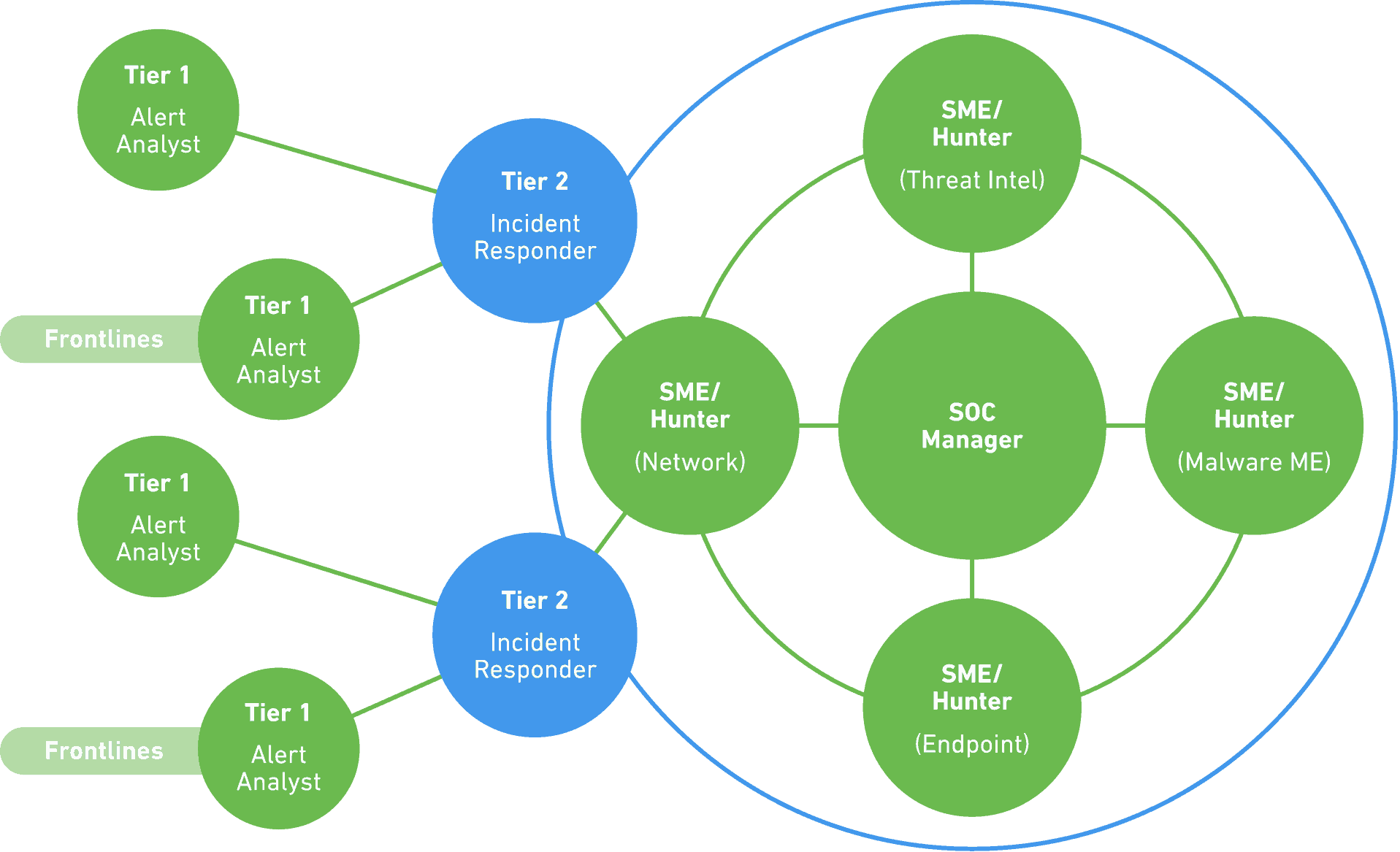
Defines design thumb rules and parameters for SOC Design. Penetration testing will simulate cyberattacks to determine potential entry methods and other vulnerabilities. Abstract A Security Operation Center SOC is made up of five distinct modules. This position fulfils the most critical role of primarily deploying the customized big data open source SOC technologies along with traditional commercial products at times in the right location and configuration to identify the. This paper discusses the functional architecture needed to integrate five distinct modules of a Security Operation Center and introduces the concepts behind each module and briefly describe common problems encountered with each of them.

In the past he has helped build security operation centers as well as run a public threat intelligence service. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Ad Help analysts navigate high-value activities and high fidelity threats. Ad Kontrollraum- Leitstellenplanung. Building Operating and Maintaining your SOC focuses on the technology and services associated with most modern SOC environments including an overview of best practices for data collection how data is processed so that it can be used for security analysis vulnerability management and some operation.
 Source: pinterest.com
Source: pinterest.com
Over the past decade information technology has. Planung Rechenzentrum Kontrollräume vom Profi. Building Operating and Maintaining your SOC focuses on the technology and services associated with most modern SOC environments including an overview of best practices for data collection how data is processed so that it can be used for security analysis vulnerability management and some operation. In the past he has helped build security operation centers as well as run a public threat intelligence service. Cybersecurity Operations Center CSOC Computer Emergency Response Team CERT In order for an organization to be considered a SOC it must.
 Source: pinterest.com
Source: pinterest.com
Abstract A Security Operation Center SOC is made up of five distinct modules. Bhsdhs Goals Objectives Benchmarks year 2000 gibb0. Learn more about Designing and Building Security Operations Center from publisher Syngress. Planung Rechenzentrum Kontrollräume vom Profi. Security operations center best practices include preemptively addressing weak points to neutralize potential attacks before they occur minimizing the number of incidents requiring an active response.

Penetration testing will simulate cyberattacks to determine potential entry methods and other vulnerabilities. Ad Kontrollraum- Leitstellenplanung. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Building a Next-Generation Security Operation Center Based on IBM QRadar and. Designing and Building Security Operations Center.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Remediation Recovery and Assessment Audit. Building a Next-Generation Security Operation Center Based on IBM QRadar and. Provide a means for constituents to report suspected cybersecurity incidents. Bhsdhs Goals Objectives Benchmarks year 2000 gibb0. Sp24 design a share point 2013 architecture the basics Alexander Meijers.
 Source: docs.microsoft.com
Source: docs.microsoft.com
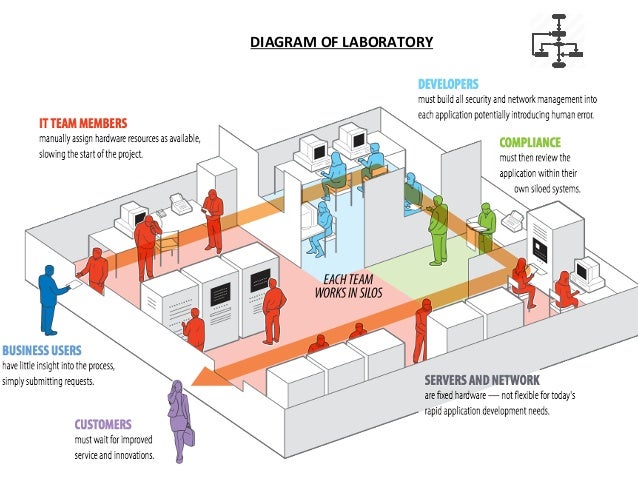
2 This hasn t changed. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. These include Event Classification. Without a SOC there is often a siloed incomplete visibility which leads to a weaker.
 Source: techtarget.com
Source: techtarget.com
This paper discusses the functional architecture needed to integrate five distinct modules of a Security Operation Center and introduces the concepts behind each module and briefly describe common problems encountered with each of them. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Building a Next-Generation Security Operation Center Based on IBM QRadar and. Planung Rechenzentrum Kontrollräume vom Profi. In the past he has helped build security operation centers as well as run a public threat intelligence service.
 Source: pinterest.com
Source: pinterest.com
This paper discusses the functional architecture needed to integrate five distinct modules of a Security Operation Center and introduces the concepts behind each module and briefly describe common problems encountered with each of them. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. But there are a lot of terms that are often used interchangeably when people describe a security operations center. Download your free copy of the 10 Essential Capabilities of a Modern SOC. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes.
 Source: in.pinterest.com
Source: in.pinterest.com
Security operations center best practices include preemptively addressing weak points to neutralize potential attacks before they occur minimizing the number of incidents requiring an active response. Event generators event collectors message database. Establish the key processes youll need to build a security operations center. Defines design thumb rules and parameters for SOC Design. While aiming to harness this potential companies are lacking sufficiently skilled cybersecurity.
 Source: pinterest.com
Source: pinterest.com
Building a Next-Generation Security Operation Center Based on IBM QRadar and. Rothke rsa 2012 building a security operations center soc Ben Rothke. EY is seeking a Cybersecurity Security Operations Center SOC Architect who wants to join an elite team and have access to the latest global technologies. Raum-Konzeption Möblierung aus einer Hand. Event generators event collectors message database.
 Source: docs.vmware.com
Source: docs.vmware.com
While aiming to harness this potential companies are lacking sufficiently skilled cybersecurity. These include Event Classification. Examine how AlienVault USM AlienVault Labs and AlienVault OTX support these critical processes. Cybersecurity Operations Center CSOC Computer Emergency Response Team CERT In order for an organization to be considered a SOC it must. Learn more about Designing and Building Security Operations Center from publisher Syngress.
 Source: pinterest.com
Source: pinterest.com
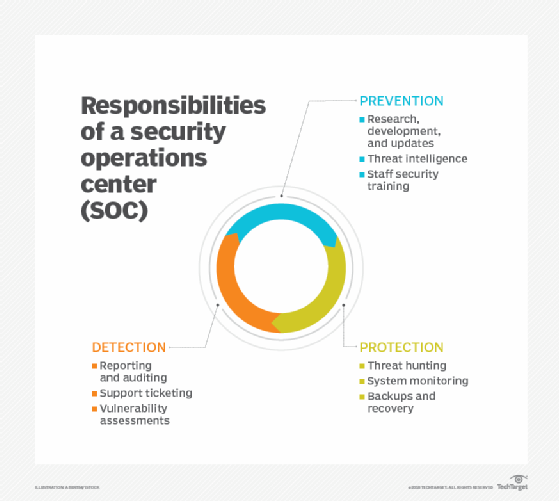
Over the past decade information technology has. Penetration testing will simulate cyberattacks to determine potential entry methods and other vulnerabilities. Proactive design and con guration ongoing monitoring of system state detection of unintended actions or undesirable state and minimizing damage from unwanted effects. Security Operations Center SOC. At checkout use discount code PBTY25 for 25 off these and other Elsevier titles.
![]() Source: content.microfocus.com
Source: content.microfocus.com
Building Operating and Maintaining your SOC focuses on the technology and services associated with most modern SOC environments including an overview of best practices for data collection how data is processed so that it can be used for security analysis vulnerability management and some operation. Building a Next-Generation Security Operation Center Based on IBM QRadar and. In the past he has helped build security operation centers as well as run a public threat intelligence service. Provide a means for constituents to report suspected cybersecurity incidents. Ad Help analysts navigate high-value activities and high fidelity threats.

Without a SOC there is often a siloed incomplete visibility which leads to a weaker. Defines the approach flow for SOC building and various components and phases involved. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Ad Kontrollraum- Leitstellenplanung. Security Operations Center SOC.

Designing and Building Security Operations Center. Ad Help analysts navigate high-value activities and high fidelity threats. Learn more about Designing and Building Security Operations Center from publisher Syngress. Establish the key processes youll need to build a security operations center. Without a SOC there is often a siloed incomplete visibility which leads to a weaker.

Ad Help analysts navigate high-value activities and high fidelity threats. Designing and Building Security Operations Center. Building Operating and Maintaining your SOC focuses on the technology and services associated with most modern SOC environments including an overview of best practices for data collection how data is processed so that it can be used for security analysis vulnerability management and some operation. This paper discusses the functional architecture needed to integrate five distinct modules of a Security Operation Center and introduces the concepts behind each module and briefly describe common problems encountered with each of them. Establish the key processes youll need to build a security operations center.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.