Your What are the layers in security architecture design images are ready. What are the layers in security architecture design are a topic that is being searched for and liked by netizens today. You can Find and Download the What are the layers in security architecture design files here. Download all royalty-free vectors.
If you’re searching for what are the layers in security architecture design pictures information linked to the what are the layers in security architecture design keyword, you have visit the right blog. Our website always gives you suggestions for refferencing the highest quality video and picture content, please kindly surf and find more informative video content and images that fit your interests.
What Are The Layers In Security Architecture Design. Layered security is a network security approach that uses several components to protect your operations with multiple levels of security measure. Daily patches and bug fixes of operating systems browsers and other commonly used applications highlight the importance of security and security assur-ance. A building block is a package of functionality designed to meet the business needs across an organization. There are seven design principles for security in the cloud.
 Archimate Example Enterprise Architecture Project Management Tools Architecture Design From pinterest.com
Archimate Example Enterprise Architecture Project Management Tools Architecture Design From pinterest.com
Identify extended enterprise units - those units outside the scoped enterprise who will need to enhance their security architecture for interoperability purposes. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing. Also called the virtualization layer the infrastructure layer is where all the servers are pooled together into one. A LAYERED SECURITY ARCHITECTURE. SOC central enterprise security toolset. Apply to all layers for example edge of network VPC load balancing every instance and compute service operating system application and code.
The infrastructure layer takes care of the hardware and the network.
A generic list of security architecture layers is as follows. The Human Layer Humans are the weakest link in any cybersecurity posture. It introduces world-class scalability and the technology of virtualization into cloud computing. Daily patches and bug fixes of operating systems browsers and other commonly used applications highlight the importance of security and security assur-ance. Apply security at all layers. It determines how the pull-down.
 Source: pinterest.com
Source: pinterest.com
This layer would also include DLP and Web Proxy tools. If Design Build then the Main Contractor will also have responsibility for design. SOC central enterprise security toolset. A generic list of security architecture layers is as follows. Identify extended enterprise units - those units outside the scoped enterprise who will need to enhance their security architecture for interoperability purposes.
 Source: pinterest.com
Source: pinterest.com
Apply a defense in depth approach with multiple security controls. SOC central enterprise security toolset. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing. This is the layer that presents the functions methods and procedures of the system based on the business rules layer. It defines how the application looks.
 Source: pinterest.com
Source: pinterest.com
In both cases the Main Contractor influences product selection. The yellow layer represents IAM a foundational layer of cloud security architectureeven if not the new perimeter completely. This layer would also include DLP and Web Proxy tools. In agencies with collaborative working relationships between enterprise architecture and information security programs both of which commonly. Security architecture roadmaps - or in other words a list of individual work packages that will define the target security architecture and show progression from the as-is state to the desired state within agreed timelines.
 Source: pinterest.com
Source: pinterest.com
Apply to all layers for example edge of network VPC load balancing every instance and compute service operating system application and code. But in DB then the Main Contractor may even provide the Architect with a list. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing. If Traditional then the Main Contractors role is to build what the architect designs. Daily patches and bug fixes of operating systems browsers and other commonly used applications highlight the importance of security and security assur-ance.
 Source: pinterest.com
Source: pinterest.com
It determines how the pull-down. To build a secure cloud architecture implementation. Human security controls include phishing simulations and access management controls that protect mission critical assets from a wide variety of human threats including cyber criminals malicious insiders and negligent users. The three dominant cloud security architecture design patterns are the federated identity pattern the gatekeeper pattern and the valet key or token that conveys specific rights to access a resource. In both cases the Main Contractor influences product selection.
 Source: pinterest.com
Source: pinterest.com
Layered security is a network security approach that uses several components to protect your operations with multiple levels of security measure. A building block is a package of functionality designed to meet the business needs across an organization. If Traditional then the Main Contractors role is to build what the architect designs. Applications In our previous IDE. It introduces world-class scalability and the technology of virtualization into cloud computing.
 Source: pinterest.com
Source: pinterest.com
To build a secure cloud architecture implementation. The infrastructure layer takes care of the hardware and the network. This is the layer that interacts with users through screens forms menus reports etc. Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the University and enable local innovation. A generic list of security architecture layers is as follows.
 Source: pinterest.com
Source: pinterest.com
SOC central enterprise security toolset. Identify soft enterprise units - those who will see change to their capability and work with core units but are otherwise not directly affected. Unlike the OSI model the layers of security architecture do not have standard names that are universal across all architectures. Security architecture building blocks. A building block is a package of functionality designed to meet the business needs across an organization.
 Source: pinterest.com
Source: pinterest.com
Daily patches and bug fixes of operating systems browsers and other commonly used applications highlight the importance of security and security assur-ance. For this an organization needs to build large data centers. To build a secure cloud architecture implementation. It introduces world-class scalability and the technology of virtualization into cloud computing. In both cases the Main Contractor influences product selection.
 Source: pinterest.com
Source: pinterest.com
Daily patches and bug fixes of operating systems browsers and other commonly used applications highlight the importance of security and security assur-ance. There are seven design principles for security in the cloud. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing. For this an organization needs to build large data centers. DESIGN ISSUES 1 INTRODUCTION System security is a key technology to the development and deployment of IT applications and services in a growing global network.
 Source: pinterest.com
Source: pinterest.com
This is the layer that presents the functions methods and procedures of the system based on the business rules layer. Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the University and enable local innovation. DESIGN ISSUES 1 INTRODUCTION System security is a key technology to the development and deployment of IT applications and services in a growing global network. Identify extended enterprise units - those units outside the scoped enterprise who will need to enhance their security architecture for interoperability purposes. Security architecture building blocks.
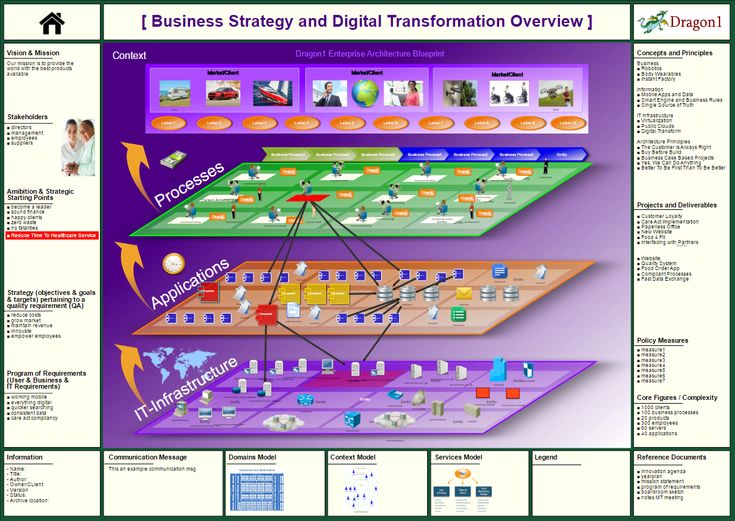 Source: pinterest.com
Source: pinterest.com
But in DB then the Main Contractor may even provide the Architect with a list. This layer represents the SOC toolsets which must be informed to make security information actionable. But in DB then the Main Contractor may even provide the Architect with a list. If Design Build then the Main Contractor will also have responsibility for design. Applications In our previous IDE.
 Source: pinterest.com
Source: pinterest.com
Security architecture roadmaps - or in other words a list of individual work packages that will define the target security architecture and show progression from the as-is state to the desired state within agreed timelines. Security architecture building blocks. SOC central enterprise security toolset. User interaction layer. This layer represents the SOC toolsets which must be informed to make security information actionable.
 Source: pinterest.com
Source: pinterest.com
SOC central enterprise security toolset. Apply a defense in depth approach with multiple security controls. Security Architecture involves the design of inter- and intra-enterprise security solutions to meet client business requirements in application and infrastructure areas. Architects performing Security Architecture work must be capable of defining detailed technical requirements for security and designing documenting and assuring functional and operational architectures. There are seven design principles for security in the cloud.
 Source: pinterest.com
Source: pinterest.com
But in DB then the Main Contractor may even provide the Architect with a list. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing. The yellow layer represents IAM a foundational layer of cloud security architectureeven if not the new perimeter completely. User interaction layer. But in DB then the Main Contractor may even provide the Architect with a list.
 Source: pinterest.com
Source: pinterest.com
Automate security best practices. The Human Layer Humans are the weakest link in any cybersecurity posture. In both cases the Main Contractor influences product selection. Also called the virtualization layer the infrastructure layer is where all the servers are pooled together into one. These layers are infrastructure platform software and an added layer of BPO Business Process Outsourcing.
 Source: pinterest.com
Source: pinterest.com
A building block is a package of functionality designed to meet the business needs across an organization. If Traditional then the Main Contractors role is to build what the architect designs. Unlike the OSI model the layers of security architecture do not have standard names that are universal across all architectures. SOC central enterprise security toolset. It introduces world-class scalability and the technology of virtualization into cloud computing.
 Source: pinterest.com
Source: pinterest.com
It is the most visible layer of the application. The yellow layer represents IAM a foundational layer of cloud security architectureeven if not the new perimeter completely. A LAYERED SECURITY ARCHITECTURE. The three dominant cloud security architecture design patterns are the federated identity pattern the gatekeeper pattern and the valet key or token that conveys specific rights to access a resource. The infrastructure layer takes care of the hardware and the network.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title what are the layers in security architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






