Your Who security operation center architecture design images are ready in this website. Who security operation center architecture design are a topic that is being searched for and liked by netizens today. You can Download the Who security operation center architecture design files here. Find and Download all royalty-free photos and vectors.
If you’re looking for who security operation center architecture design images information related to the who security operation center architecture design interest, you have visit the ideal site. Our site always gives you hints for downloading the highest quality video and picture content, please kindly search and find more informative video articles and graphics that fit your interests.
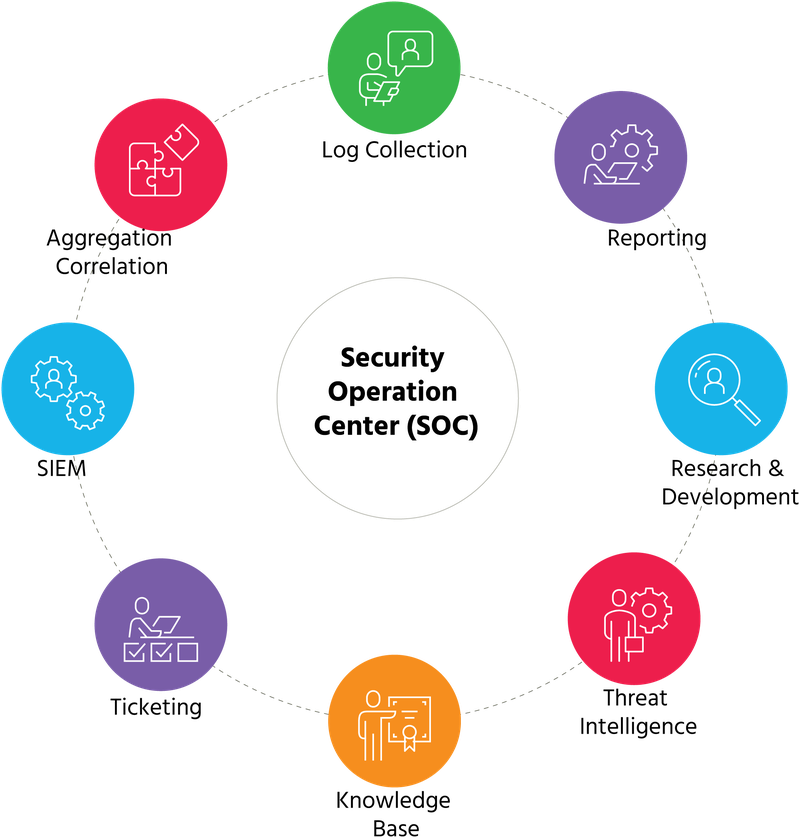
Who Security Operation Center Architecture Design. Defines the approach flow for SOC building and various components and phases involved. To get the best out of your investment you should operate the various SOC technologies under a cohesive architecture. A software or hardware specialist who focuses on security aspects in the design of information systems. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC.
 Pin On Corporate From pinterest.com
Pin On Corporate From pinterest.com
Ad Help analysts navigate high-value activities and high fidelity threats. An issue tracking system or ticket system is a vital part of your operation center. The SOC manager often fights fires within and outside of the SOC. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. This document is not intended to establish the requirement for an EOC or establish the operational procedures of an EOC.
OPERATION CENTER INFRASTRUCTURE.
Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC. This document is not intended to establish the requirement for an EOC or establish the operational procedures of an EOC. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Proactive design and configuration ongoing monitoring of system state detection of unintended actions or undesirable state and minimizing damage from unwanted effects. Creates solutions and tools that help organizations deal robustly with disruption of operations or malicious attack.
 Source: pinterest.com
Source: pinterest.com
A security operation centers core ability must be to avoid security failures that have a direct impact on the brand andor disrupt the overall growth of the company. They must also take into account the organizations business culture. The management of information security operations is a complex task especially in a cloud environment. The journey begins with a review of important concepts relevant to information security and security operations. Download your free copy of the 10 Essential Capabilities of a Modern SOC.
 Source: pinterest.com
Source: pinterest.com
Fordere jetzt Dein Infomaterial an. This demands that people processes and technology grow organically to protect core technologies adapt to changing business conditions and prepare for and respond to global threats without impacting. The cloud service layers and multi-tenancy architecture creates a complex environment in. This book focuses on the best practices to develop and operate a security operations center SOC. This chapter opens with a discussion about the continuously evolving security landscape and how new cybersecurity challenges impact how we perceive security.
 Source: fool.com
Source: fool.com
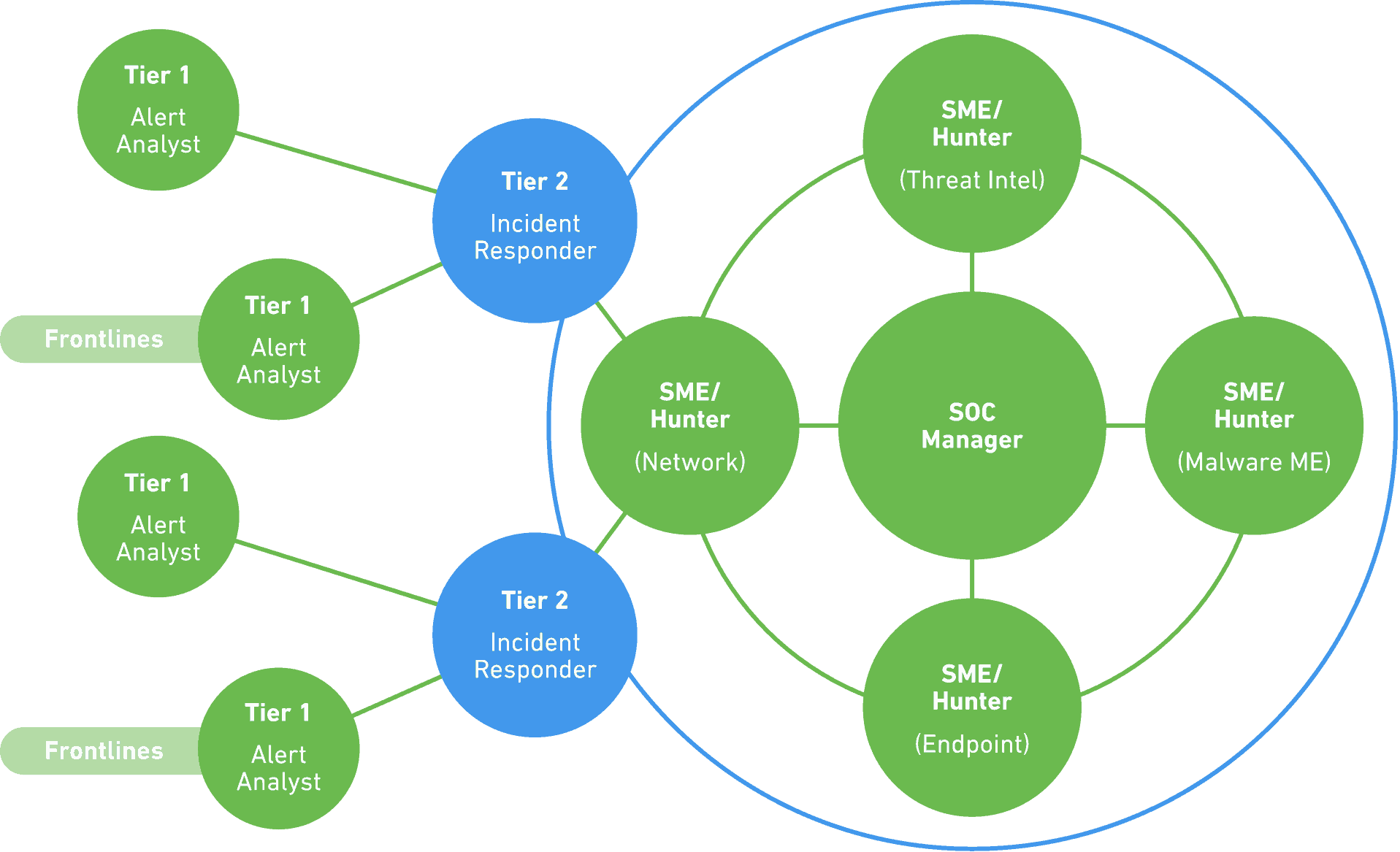
Download your free copy of the 10 Essential Capabilities of a Modern SOC. Studiere an Deutschlands beliebtester Fernhochschule. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC. Security information and event management SIEM and log management LM best practices Section 83 Joe Judge and Eugene Aronne. In addition to SOC analysts a security operations center requires a ringmaster for its many moving parts.
 Source: pinterest.com
Source: pinterest.com
The architecture should formalize the operation model of SOC in terms of components and relationships. You need to be able to create update and resolve reported issues as well as track work progress. Defines the approach flow for SOC building and various components and phases involved. Sometimes employed within the SOC and sometimes supporting the SOC as part of development or operations teams. This chapter opens with a discussion about the continuously evolving security landscape and how new cybersecurity challenges impact how we perceive security.
 Source: pinterest.com
Source: pinterest.com
This book focuses on the best practices to develop and operate a security operations center SOC. Download your free copy of the 10 Essential Capabilities of a Modern SOC. As your data needs increase you may need a security operations center SOC to protect your data. Original work on intrusion detection systems IDS and SIEM Section 82 and Section 83 Frank Posluszny. Ad Studiere Architektur am Standort in Frankfurt oder am virtuellen Campus.
 Source: exabeam.com
Source: exabeam.com
Ad Help analysts navigate high-value activities and high fidelity threats. SOC Clients Dashboard andor reports that reflect organizational risk status and security trends CIO Report interface to key security metrics Auditor Compliance oriented reporting that reflects current status against the organizations key security objectives Security Officer Operational dashboard that highlights areas of risk or immediate threat and enables. The architecture should formalize the operation model of SOC in terms of components and relationships. You need to be able to create update and resolve reported issues as well as track work progress. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security.
 Source: pinterest.com
Source: pinterest.com
Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC. Creates solutions and tools that help organizations deal robustly with disruption of operations or malicious attack. Security operations center staff consists primarily of security analysts who work together to detect analyze respond to report. The management of information security operations is a complex task especially in a cloud environment. Ad Help analysts navigate high-value activities and high fidelity threats.
 Source: pinterest.com
Source: pinterest.com
Ad Help analysts navigate high-value activities and high fidelity threats. This book focuses on the best practices to develop and operate a security operations center SOC. Fordere jetzt Dein Infomaterial an. Proactive design and configuration ongoing monitoring of system state detection of unintended actions or undesirable state and minimizing damage from unwanted effects. Initial concept and development of material on.
 Source: pinterest.com
Source: pinterest.com
Security information and event management SIEM and log management LM best practices Section 83 Joe Judge and Eugene Aronne. They must also take into account the organizations business culture. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. The goal is to capture common and best practices provide defendable metrics that can be used to justify SOC resources to. SOC Clients Dashboard andor reports that reflect organizational risk status and security trends CIO Report interface to key security metrics Auditor Compliance oriented reporting that reflects current status against the organizations key security objectives Security Officer Operational dashboard that highlights areas of risk or immediate threat and enables.
 Source: pinterest.com
Source: pinterest.com
The goal is to capture common and best practices provide defendable metrics that can be used to justify SOC resources to. This book focuses on the best practices to develop and operate a security operations center SOC. A software or hardware specialist who focuses on security aspects in the design of information systems. This demands that people processes and technology grow organically to protect core technologies adapt to changing business conditions and prepare for and respond to global threats without impacting. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC.
 Source: in.pinterest.com
Source: in.pinterest.com
The management of information security operations is a complex task especially in a cloud environment. Spokes of this model can incorporate a variety of systems such as vulnerability assessment solutions governance risk and compliance GRC systems application and database scanners. This 2019 edition of the SANS Security Operations Center SOC Survey was designed to provide objective data to security leaders and practitioners who are looking to establish a SOC or optimize their existing SOCs. Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITREs. To get the best out of your investment you should operate the various SOC technologies under a cohesive architecture.
 Source: pinterest.com
Source: pinterest.com
They must also take into account the organizations business culture. The goal is to capture common and best practices provide defendable metrics that can be used to justify SOC resources to. SOC Clients Dashboard andor reports that reflect organizational risk status and security trends CIO Report interface to key security metrics Auditor Compliance oriented reporting that reflects current status against the organizations key security objectives Security Officer Operational dashboard that highlights areas of risk or immediate threat and enables. The cloud service layers and multi-tenancy architecture creates a complex environment in. Creates solutions and tools that help organizations deal robustly with disruption of operations or malicious attack.
 Source: pinterest.com
Source: pinterest.com
Ad Studiere Architektur am Standort in Frankfurt oder am virtuellen Campus. Security operations center staff consists primarily of security analysts who work together to detect analyze respond to report. Original work on intrusion detection systems IDS and SIEM Section 82 and Section 83 Frank Posluszny. Defines the approach flow for SOC building and various components and phases involved. The journey begins with a review of important concepts relevant to information security and security operations.
 Source: pinterest.com
Source: pinterest.com
SOCs have been typically built around a hub-and-spoke architecture where a security information and event management SIEM system aggregates and correlates data from security feeds. Original work on intrusion detection systems IDS and SIEM Section 82 and Section 83 Frank Posluszny. Ad Help analysts navigate high-value activities and high fidelity threats. Just using a single security tool in your infrastructure may not be sufficient to properly analyze an event though using all of. As your data needs increase you may need a security operations center SOC to protect your data.
 Source: pinterest.com
Source: pinterest.com
Original work on intrusion detection systems IDS and SIEM Section 82 and Section 83 Frank Posluszny. Security information and event management SIEM and log management LM best practices Section 83 Joe Judge and Eugene Aronne. Rather than being focused on developing security strategy designing security architecture or implementing protective measures the SOC team is responsible for the ongoing operational component of enterprise information security. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC. The cloud service layers and multi-tenancy architecture creates a complex environment in.
 Source: pinterest.com
Source: pinterest.com
This chapter opens with a discussion about the continuously evolving security landscape and how new cybersecurity challenges impact how we perceive security. Proactive design and configuration ongoing monitoring of system state detection of unintended actions or undesirable state and minimizing damage from unwanted effects. Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITREs. Commanders security personnel planners designers architects and engineers should use this document when planning or designing an EOC. This UFC has been coordinated with the.
 Source: pinterest.com
Source: pinterest.com
Studiere an Deutschlands beliebtester Fernhochschule. A security operation centers core ability must be to avoid security failures that have a direct impact on the brand andor disrupt the overall growth of the company. Fordere jetzt Dein Infomaterial an. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Ad Help analysts navigate high-value activities and high fidelity threats.
 Source: pinterest.com
Source: pinterest.com
For the planning and design of Emergency Operation Centers EOCs. Sometimes employed within the SOC and sometimes supporting the SOC as part of development or operations teams. The architecture should formalize the operation model of SOC in terms of components and relationships. Ad Help analysts navigate high-value activities and high fidelity threats. A security operation centers core ability must be to avoid security failures that have a direct impact on the brand andor disrupt the overall growth of the company.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title who security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






